Caesar Cipher in PythonIn this tutorial, we will explore one of the encryption methods called Caesar Cipher. It is a part of Cryptography. IntroductionIn this technique, each character is substituted by a letter certain fixed number position it's later or before the alphabet. For example - Alphabet B is replaced by two positions down D. D would become F and so on. This method is named after popular frictional characters Julius Caesar, who used it to communicate with officials. There is an algorithm used to implement it. Let's understand the following. Feature of Caesar Cipher AlgorithmThis algorithm consists of a few features that are given below.
There is an integer value required to define each latter of the text that has been moved down. This integer value is also known as the shift. We can represent this concept using modular arithmetic by first transmuting the letter into numbers, according to the schema, A = 0, B = 1, C = 2, D = 3…….. Z = 25. The following mathematical formula can be used to shift n letter. How to decrypt?The decryption is the same as encryption. We can create a function that will accomplish shifting in the opposite path to decrypt the original text. However, we can use the cyclic property of the cipher under the module. Cipher(n) = De-cipher(26-n) The same function can be used for decryption. Instead, we will modify the shift value such that shifts = 26 - shift. 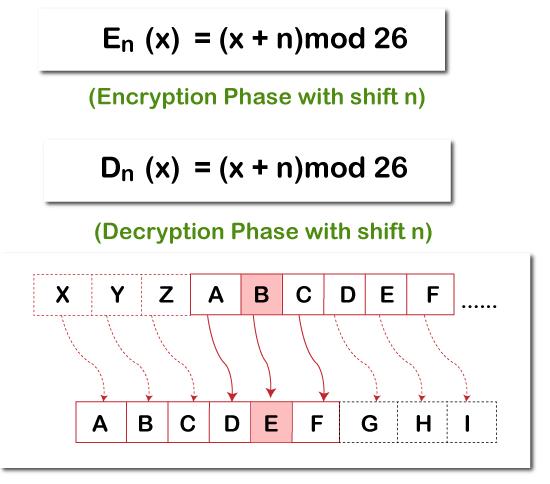 Let's understand the following example - Example - Output: Plain txt : CEASER CIPHER EXAMPLE Shift pattern : 4 Cipher: HJFXJWsHNUMJWsJCFRUQJ The above code has traversed the character at a time a time. It transferred the each character as per rule depending on the procedure of encryption and decryption of the text. We have defined few specific set of position that generated a cipher text. Breach in Caesar Cipher AlgorithmWe can hack the cipher text in various ways. One of the ways is Brute Force Technique, which involves trying every possible decryption key. This technique is not so hard and doesn't require much effort. Let's understand the following example. Example - Output: Hacking k #25: rHNUMJWrIJRTHJFXJWHJFXJW Transposition CipherTransposition cipher algorithm is a technique where the alphabet order in the plaintext is rearranged to form a cipher text. This algorithm doesn't support the actual plain text alphabets. Let's understand this algorithm using an example. Example - We will take the simple example called columnar transposition cipher where we write the each character in the pain text in horizontal with specified alphabet width. The vertically written texts are cipher, which create a completely unlike cipher text. Let's take a plain text, and apply the simple columnar transposition technique as shown below. 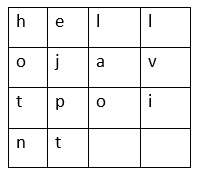 We placed the plain text horizontally and the cipher text is created with vertical format as: hotnejpt.lao.lvi. To decrypt this, the receiver must use the same table to decrypt the cipher text to plain text. Code - Let's understand the following example. Explanation - In the above code, we have created a function named split_len(), which spitted the pain text character, placed in columnar or row format. The encode() method created the cipher text with a key specifying the number of columns, and we have printed each cipher text by reading through each column. Note - The transposition technique is meant to be a significant improvement in crypto security. Cryptanalyst observed that re-encrypting the cipher text using same transposition cipher shows better security.Next TopicTokenizer in Python |

We provides tutorials and interview questions of all technology like java tutorial, android, java frameworks
G-13, 2nd Floor, Sec-3, Noida, UP, 201301, India










